The evolution of phishing: From fake invoices to job interview invitations
The job market has become a new hunting ground for cybercriminals. Instead…
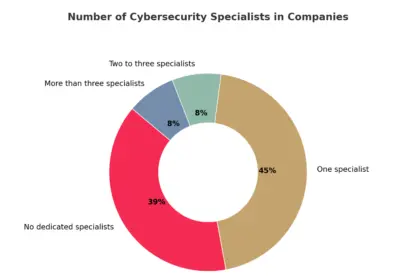
Poland’s alarming skills gap. Why are we such an easy target for hackers?
Poland's economy is at the heart of a digital paradox. On the…
The more tools, the worse? The cyber security paradox that is destroying businesses
Companies are investing in dozens of tools to protect their growing infrastructure.…
MSP 2.0: How managed service providers are transforming into strategic partners in cyber security
For years, managed service providers(MSPs) were seen as external IT teams -…
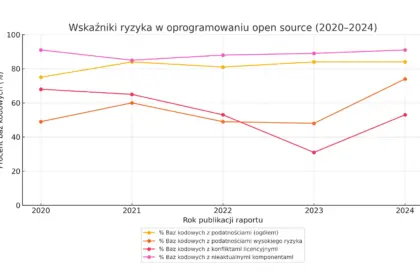
The Open Source Paradox – How innovation became the biggest threat to business
Open source software (OSS) is the silent, invisible engine driving today's digital…
Cyber insurance is not enough. Why don’t policies cover real losses after an attack?
More and more companies are investing in cyber insurance, seeing it as…
Cybersecurity in chaos: how an excess of tools is ruining IT security
In theory, every new security tool increases a company's protection. In practice…
What does a cyber attack on Microsoft SharePoint mean for business?
The ongoing 'ToolShell' cyberattack campaign against local Microsoft SharePoint servers is not…
Cyber security is not a sprint. Companies need to stop putting out fires and start planning
The increasing number of cyber attacks, new regulatory obligations and limited human…
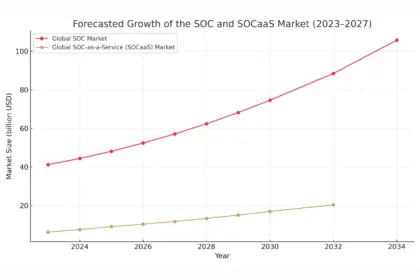
SOC report: Why modern security centres are becoming a pillar of business continuity
In a digital ecosystem where the lines between innovation and threat are…
Data Centric Security is the future. Is your IT security keeping up?
For years, IT security has been designed around one principle: strengthen the…
Cyber security OT: Why is the industry still standing still?
Despite growing cyber threats and increasing regulatory pressure, the industrial sector continues…
How deepfake is changing the tactics of social engineering attacks
Until recently, social engineering was mainly associated with a suspicious email from…
Vishing and smishing – a new wave of threats that IT is not on the radar
For years, phishing meant suspicious emails with attachments, typos and links leading…
Ransomware attack on Herbapol. Cyber criminals demand $900,000 ransom
The ransomware incident that affected Herbapol-Lublin is another wake-up call for food…
Meta vs Italy: CJEU settles dispute over publisher fees
The EU dispute over the rights of publishers and the obligations of…
Cyber attacks on the rise through Middle East conflict – companies must be vigilant
Escalating geopolitical tensions in the Middle East are increasingly translating into escalating…
EDPB simplifies RODO – new tools and support for companies
The European Data Protection Board (EDPB), responsible for coordinating compliance with the…
Citrix Bleed 2 – new NetScaler vulnerability dangerous after all? Experts have their doubts
A new vulnerability in Citrix NetScaler - designated CVE-2025-5777 and unofficially named…
Cyber attacks increase by 36% in one month
In May 2025, the cyber threat landscape became noticeably more turbulent. According…
Ingram Micro victim of ransomware attack. Global distribution operations disrupted
The failure of Ingram Micro 's systems was caused by a ransomware…